Integrating Azure Active Directory with SFTP Gateway
With version 3.004.00, you can now integrate Azure Active Directory with SFTP Gateway’s web admin portal. In other words, web admins can leverage their existing AAD credentials instead of managing another account just for SFTP Gateway.
What is Azure Active Directory?
Azure Active Directory (AAD) is a cloud-based identity and access management service from Microsoft. It serves as a central hub for managing user identities, access rights, and authentication across various Microsoft services and applications, as well as other third-party software that supports standards such as SAML, OAuth, and OpenID Connect. AAD provides a range of features, such as single sign-on, multi-factor authentication, conditional access policies, and identity protection, to help organizations ensure the security of their data and resources.
Summary of the AAD authentication process
Configuring AAD authentication is a process. At a high level, you will be performing three steps:
- Create an App Registration
- Grant users in AAD access to this App Registration
- Point SFTP Gateway to the App Registration
Create an App Registration in the Azure Portal

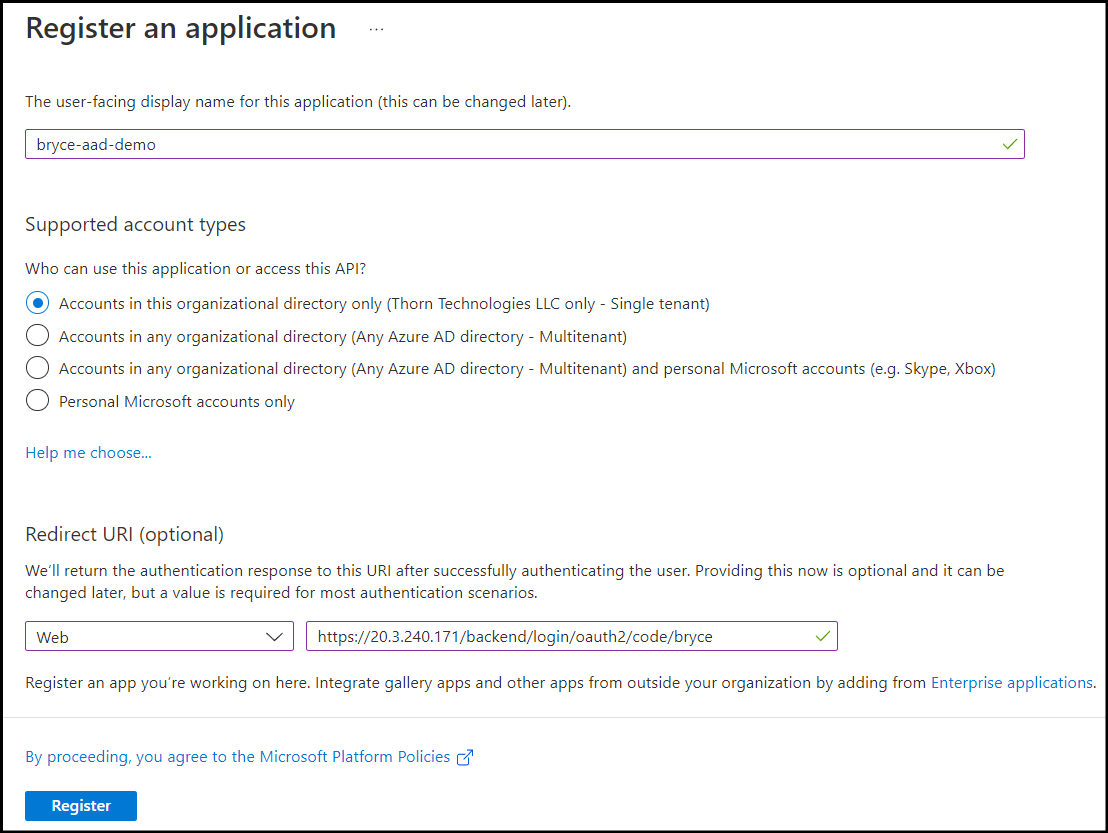
https://<sftp-gateway-hostname/backend/login/oauth2/code/<custom name>
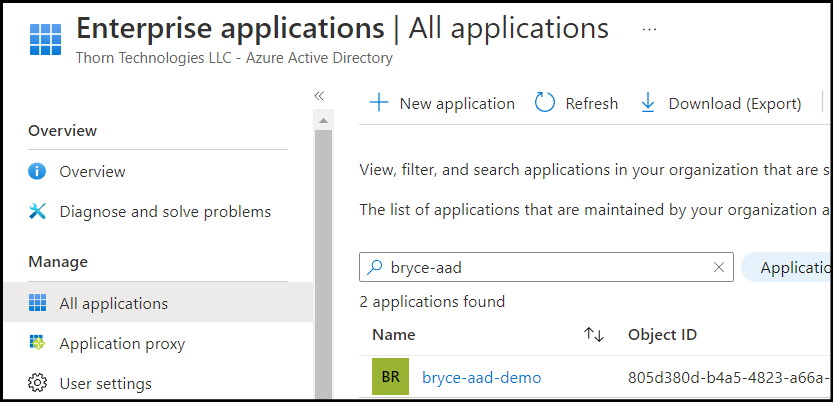
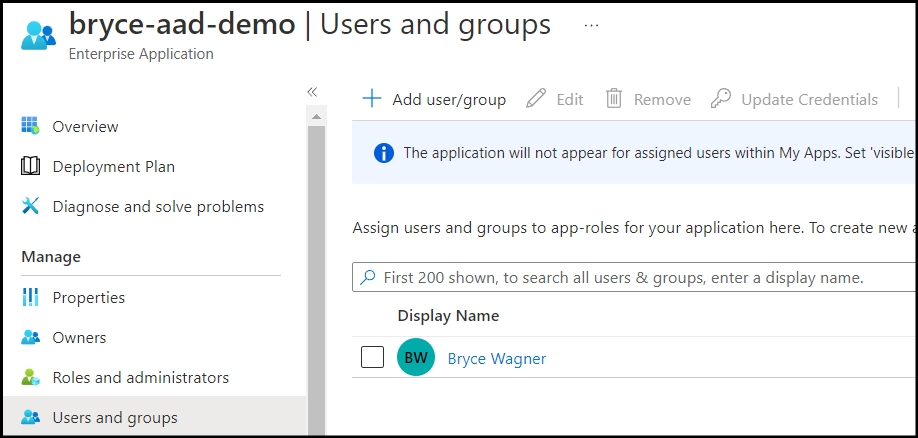
Add users in AAD


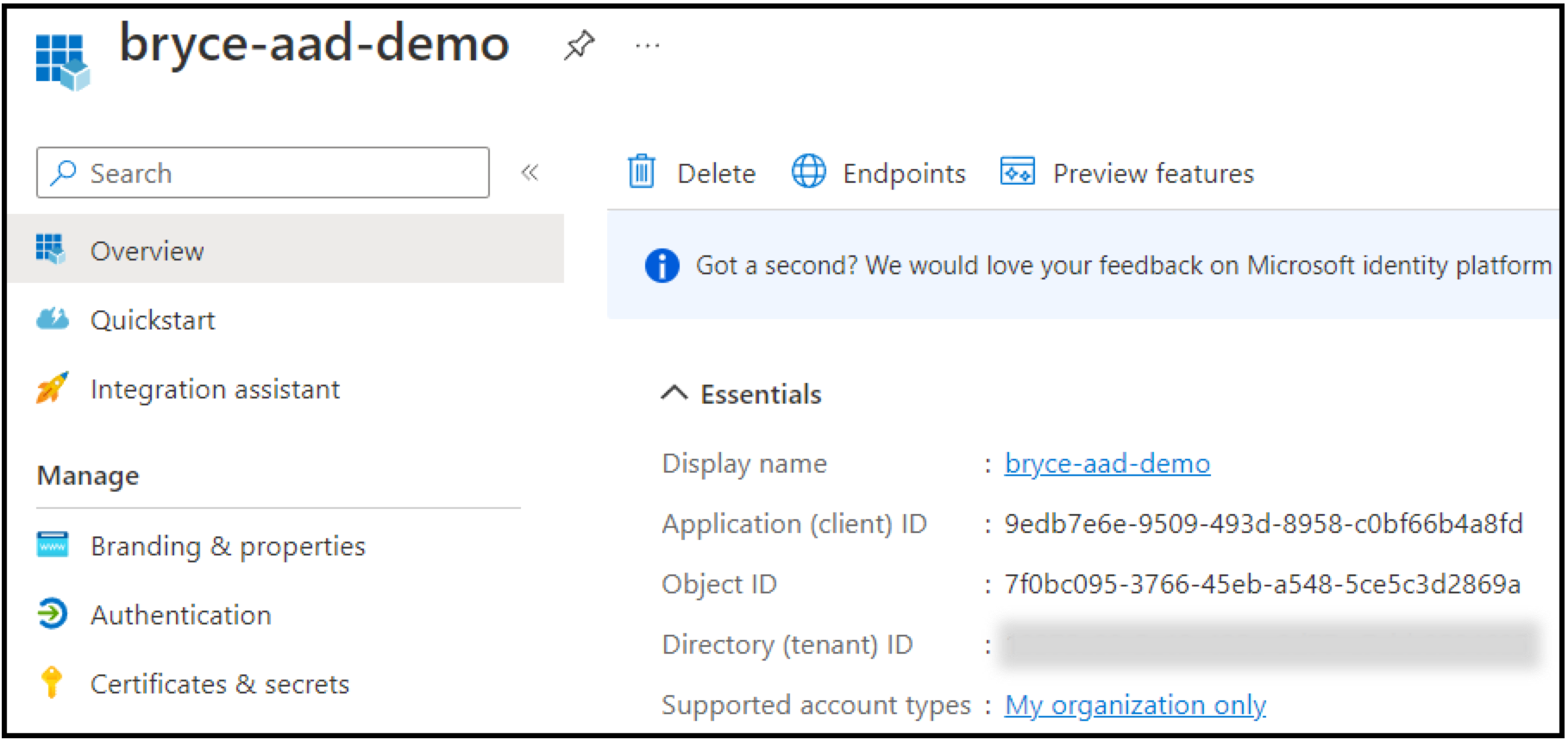
Get App Registration IDs
For the next step in integrating Azure Active Directory with SFTP Gateway, SFTP Gateway needs the App Registration IDs. In the Azure Portal, go back to App Registrations.

Configure the Identity Provider on SFTP Gateway
In the SFTP Gateway web admin portal, go to Settings. Under Identity Providers, click Add new IdP.
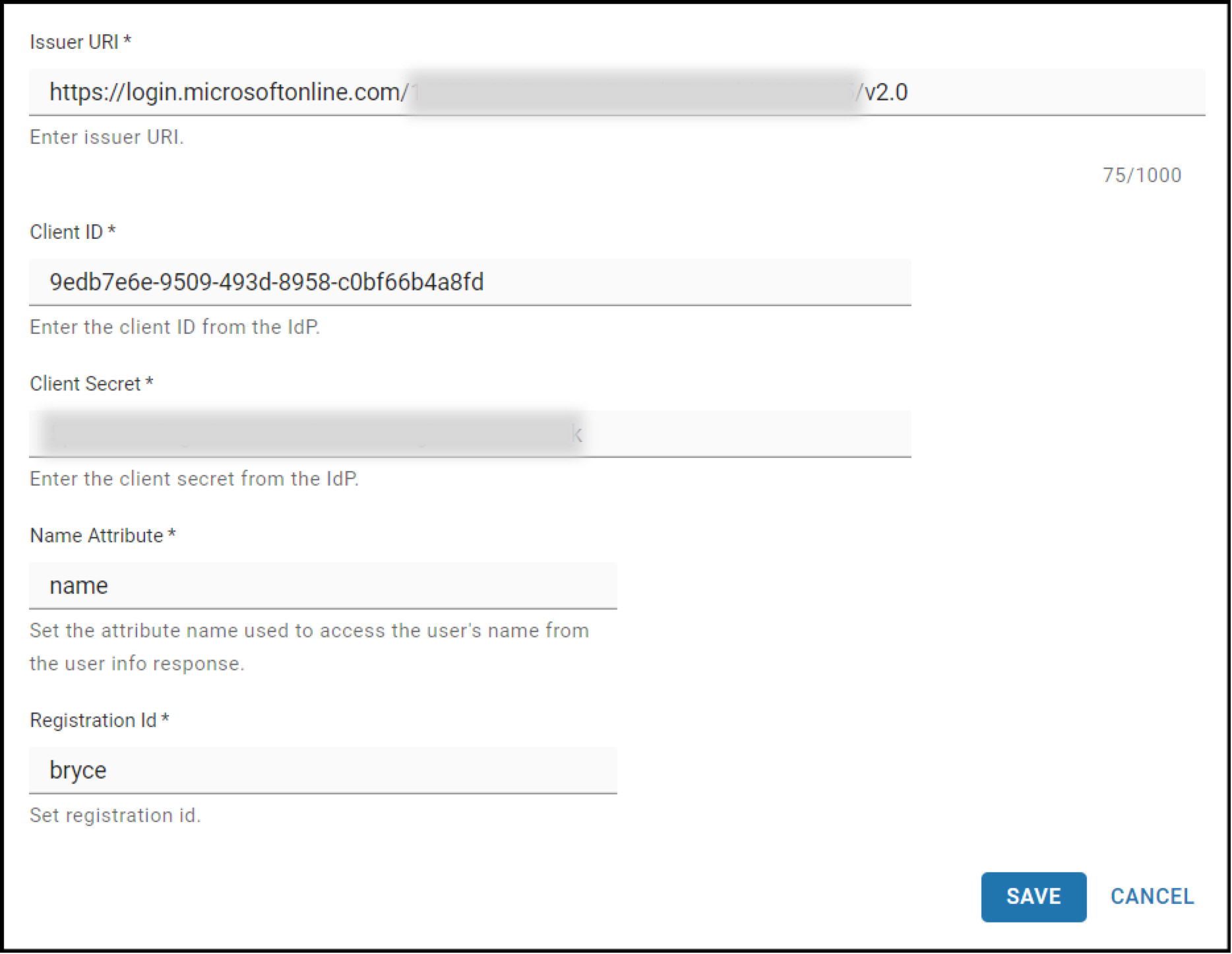
For the new Identity Provider, fill in the following fields:
- Identity Provider Display Name: This is the name for the Identity Provider that will be displayed at the login screen for Web Admin Users.
- Issuer URI: Paste in this text, https://login.microsoftonline.com/{TENANT_ID}/v2.0. Replace the placeholder value with the tenant ID you copied earlier from the overview page of the App Registration.
- Client ID: Paste in the client ID you copied earlier from the overview page of the App Registration.
- Client Secret: Paste in the client secret value you copied earlier from the Client secrets page.
- Name Attribute: Set this value to name.
- Registration ID: Use the custom name you made for the Redirect URI when creating the Registration App.
Test the changes in the web browser
If you are logged into the web admin UI, click the logout button on the top right and then refresh the browser.

You will be redirected to login.microsoftonline.com to enter your Azure credentials.
Once logged in, you will be authenticated to the SFTP Gateway web admin portal. You’ve now completed the process for integrating Azure Active Directory with SFTP Gateway.
For more on integrating AAD with SFTP Gateway, please see the Knowledge Base or our YouTube channel and the video below.


